PentesterAcademy PACES / CRTE / CRTP Labs Review
During the Great Lockdown of 2020, I decided to use the time saved not commuting by completing the red team labs offered by Pentester Academy. They offer three red team labs at the time of writing this post, which lead to the three qualifications CRTP, CRTE and PACES. I am happy to say I have passed all three and not many people have passed the PACES course so I am very happy with that. I wanted to write this post firstly as a sign of appreciation for the amazing courses, and secondly as a guide for someone considering which to start with. I will start at the easiest and work my way up them.
I would also like to give a shout out to all the support staff at PentesterAcademy. For all three courses they were amazing. Very responsive and willing to help. If I needed a lab reverted they were on it, if I needed a nudge they would help without spoiling, if something was broken they would also look into fixing it and see what the issue was. They were quick to respond and very helpful and were actually technical which was so helpful. It’s easily the best support staff I have talked too.
Certified Red Team Professional (CRTP)
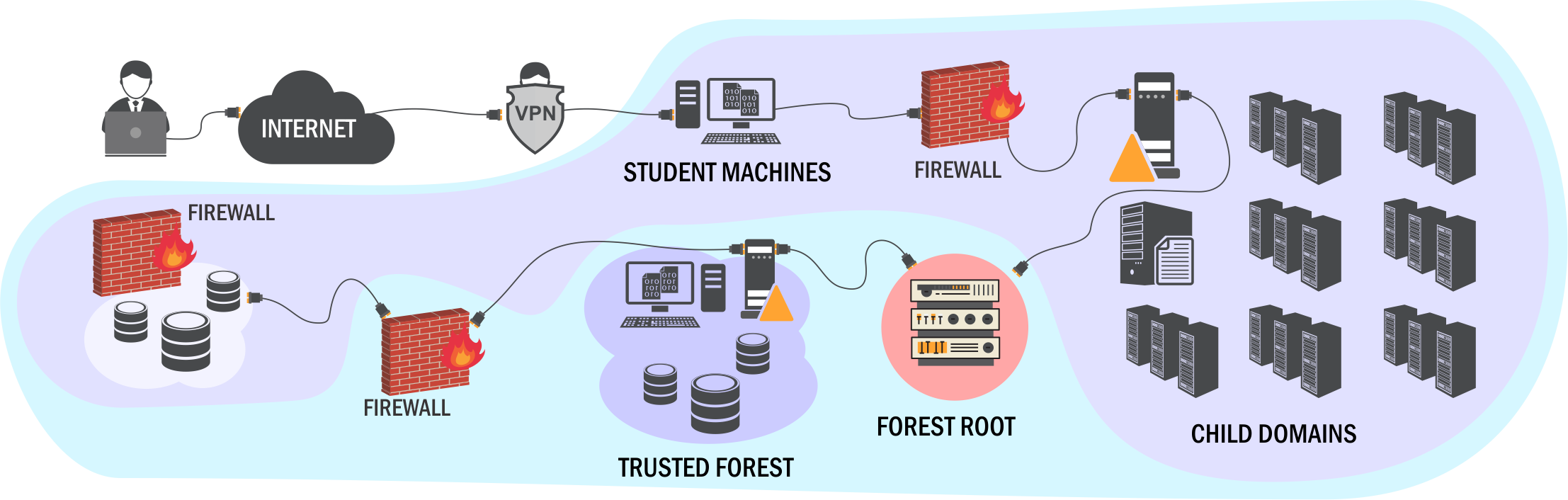
CRTP is the first of the three red team courses offered. This course is aimed at beginners of Active Directory security and is beginner friendly. This course covers attacks such as kerberoasting, ASREProasting, SetSPN, Unconstrained Delegation, Constrained Delegation, ACL Abuse, Trustpocolypse attacks and cross forest trust tickets. This isn’t an inclusive list but does give an idea of the types of attacks covered. If you are very familiar with these then it may be worth looking to do a more advanced one. If you don’t know any of those then this is for you!
Structure
The lab for CRTP consists of a few domains across two forests. The network map can be seen above or on their website. The course is laid out in a way where no attack is more than 2 jumps away. I really like the for the first one because if you wanted to say, just jump in and try an unconstrained delegation attack, you would never have to go through a long chain of attacks to get there. This makes the CRTP lab ideal for trying the attacks.
Included with CRTP is a full walkthrough of the lab including a pdf which shows all commands and output. All the tools needed are included on the machine, all you need is a VPN and RDP or you can do it all through the browser! This is amazing for a beginner course.
If that wasn’t enough, there is 14 hours of content to watch explaining all the attacks fully and showing the attacks in the lab. As you can see, this is very beginner friendly and a great start for anyone looking to learn more about AD security.
Exam
The exam for CRTP is a 24 hour exam. During this time you need to compromise the environment (not going to put much info to avoid accidental spoilers) and write a report. This is a good exam and should be ok as long as you are comfortable with the material.
One thing I will advise is to not just follow the walkthrough. When you do the CRTP lab with the walkthrough, do it again without. Do it again with different tools. Do it again with a command and control (C2) like Metasploit or Covenant. Try alternate attack routes and bypass various restrictions. If you do all this you will have no problem at all in the exam and will have multiple options.
Certified Red Team Expert (CRTE)
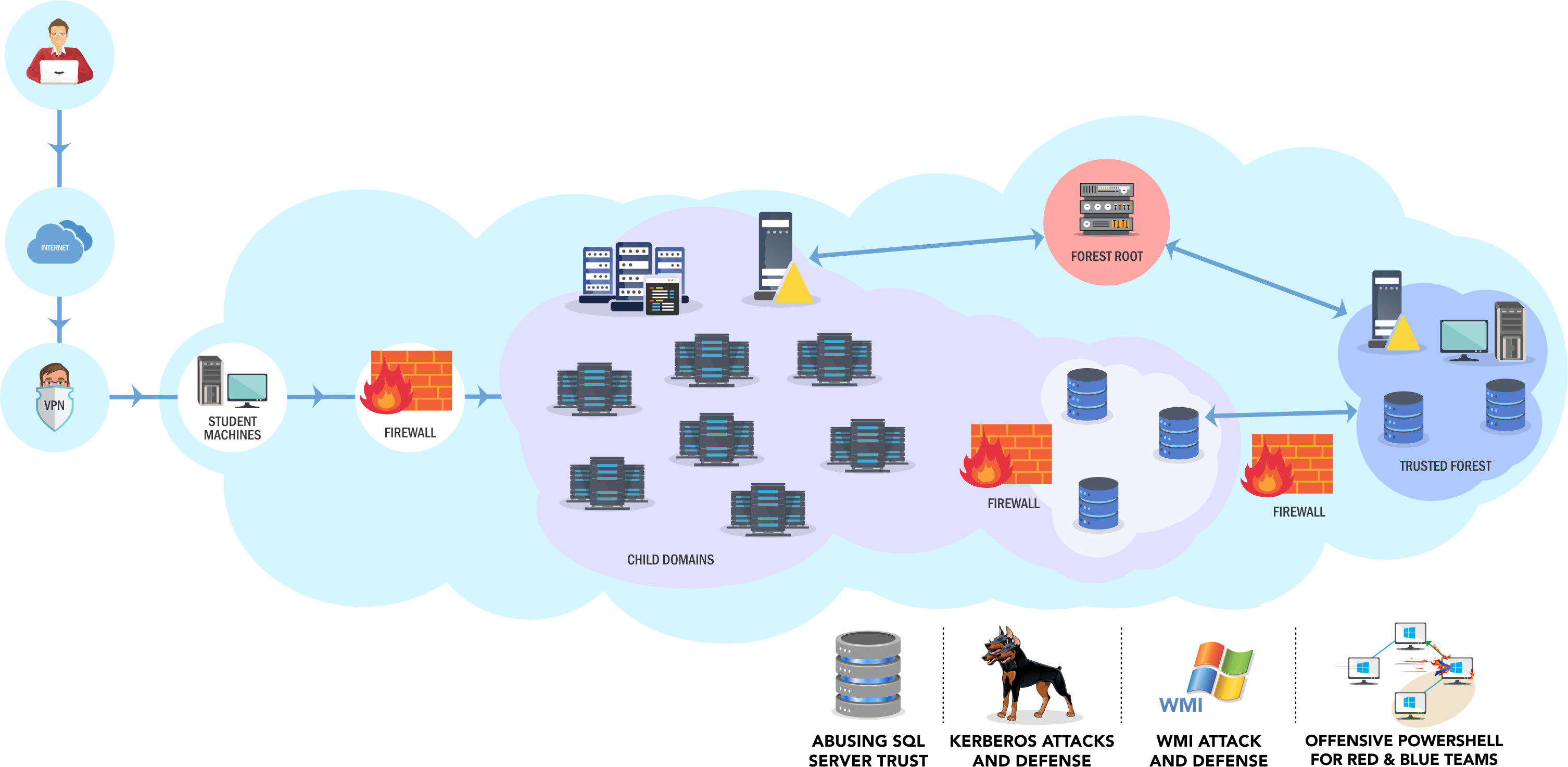
CRTE is the second of the red team courses. This course is aimed at an intermediate level. It contains similar attacks to CRTP but with a lot more MS-SQL attack potentials and a lot more logistical issues. Gone are the days where all attacks are only a hop away! You should be very comfortable with CRTP content before doing CRTE.
Structure
The lab for CRTE is the same in size to CRTP, as can be seen on the network map above. The key difference is the extra challenges put in and the difficulties in the environment and some new attack paths. This gives a playground for a lot more MS-SQL attacks, privescs, command exec and persistence techniques which is lovely. It also includes attacks such as phishing and lots of various ways to bypass application whitelisting, double-hop restrictions etc.
There are 60 flags to obtain within CRTE, 5 for each host. These typically include host based enumeration to find specific registry keys, data etc. A key focus on the flags was finding PII / PCI data such as emails and credit card details within databases which was a great touch and really useful for actual red teams where the objective is almost always PCI / PII.
There is not walkthrough for this course and the videos given are similar to before. Tools are also not included on the machine by default. This gives you the knowledge you need but you need to research and apply it appropriately, which I think is very nice. There are challenges within the lab that the course content will not help with, but I like that as it forces you to research which is a large part of pentesting.
Exam
The CRTE exam is a 48 hour exam with a similar structure to CRTP, in that its attack the lab then report. If you have done the labs and are comfortable with that then you should be fine. I would recommend getting all flags in the lab and taking good notes. Also you should know reverts are available during the exam if you ask the support staff and think something is broken. Whilst something breaking is rare, it did happen during mine and they gave me extra time as compensation which was very nice. Don’t be afraid to ask for a revert and lose a lot of time like I did.
I would once again suggest doing the lab with powershell first, then with a C2 framework. I would also urge to find new routes and attacks and take full advantage of the playground you have as there aren’t many good ones around to learn this stuff.
Pentester Academy Certified Enterprise Specialist (PACES)
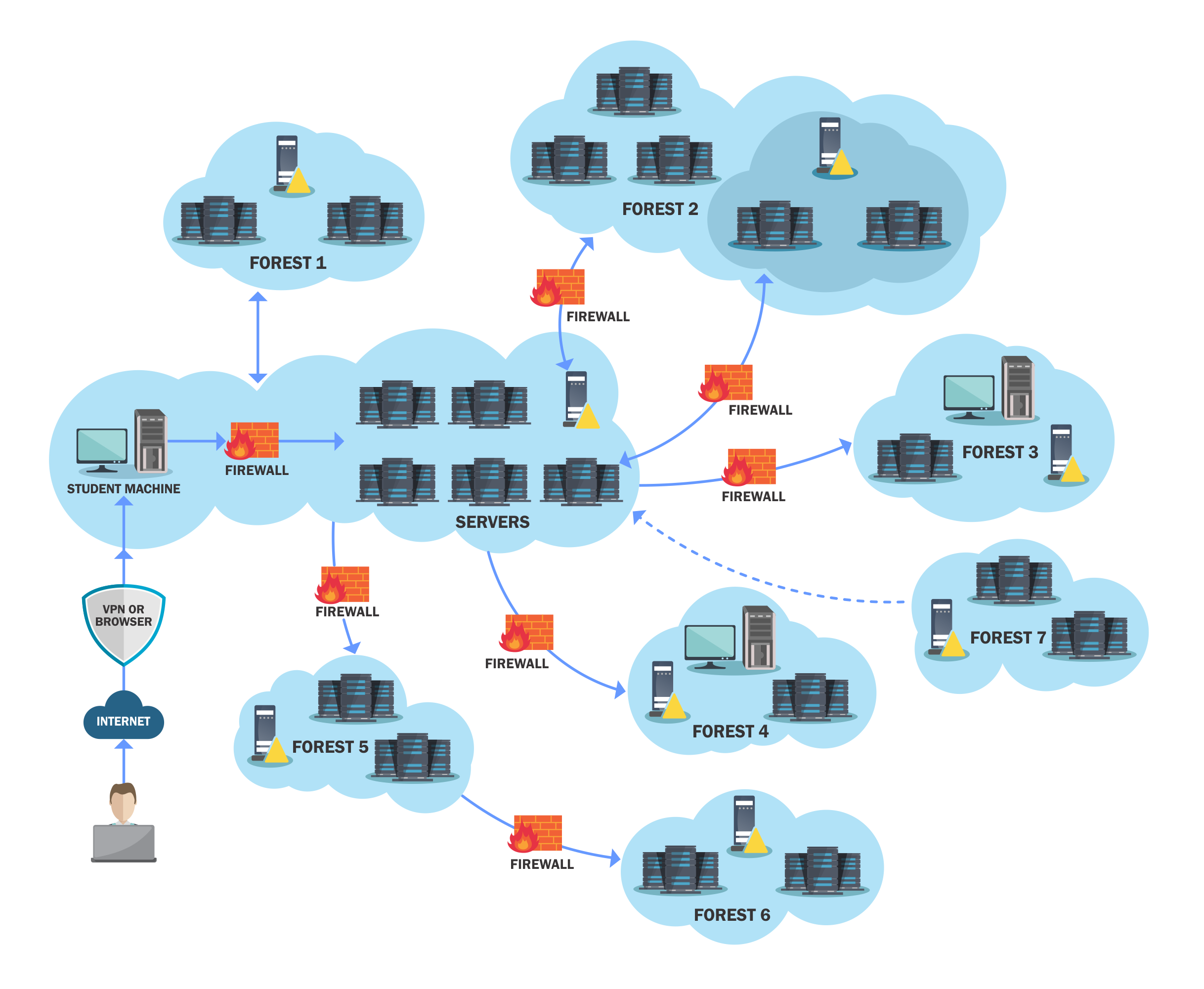
PACES is by far the hardest of the three red team certifications offered by Pentester Academy. CRTP and CRTE had only a few domains across two forests whereas PACES has a large number of forests and several of those have multiple domains. One of those forests is even not on the network map and is completely isolated…almost 😉. The size of this lab is huge compared to the others and will push you. Before doing this you should be extremely comfortable with CRTP and CRTE!
Structure
The lab is huge as mentioned. They removed the flag system and instead its objective based. The goal is to find a secret code that can be used to launch malicious bank transfers. To get there you will need to exploit attack paths such as LAPS abuse, exchange abuse, RBCD, WSUS attacks, Printer bug, JEA breakouts, PAM trusts and more. Included with all the new techniques needed is most of the old ones as well. However, in this lab all the old ways you owned those misconfigurations won’t work. You will have to find new ways to enumerate (BloodHound wont help you much with this lab) and new ways to exploit issues as they intentionally make it more difficult. This was great for me as it forces you to really understand it and have alternative ways ready for real engagements where things go wrong for weird reasons.
The lab is organized in almost a Red Forest type of architecture, so every department of GCB (Global Cyber Bank) has a different forest with often little trust between the two. You can’t just abuse cross-forest trust tickets in this lab, you need to actually find the ways to abuse cross forest permissions that users have. It’s a really interesting dynamic and is a more secure environment than most I have seen for actual pentesting. It implements the latest in defense such as LAPS, device guard, JEA, PAM trusts etc making it difficult to attack. There is also no walkthrough so you are on your own (apart from the amazing support team if you ever need a nudge).
The lab also includes an ELK stack type detection, with a splunk instance that you have full access too and can see what is going on around the environment. You can see how noisy your actions are if someone is looking at windows event logs, and this even gives you a chance to practice injecting fake logs or attempting to get machines to stop logging to hide tracks. This is a really interesting angle for an attacker. I haven’t seen any other course that allows you to see whats going on with detection whilst you attack it. I loved this!
Exam
The exam is another 48 hour exam. However this time you need to attack and defend the lab. I won’t share much, but you essentially need to use what you have learnt in the labs to own the exam environment completely, then you need to fix all of the issues that you exploited. When you compromise the last machine you will find a file on their with the cleartext passwords for all the machines so that you can log onto them and fix the issues.
The lab doesn’t prepare you much for defense, so I recommend setting up your own lab with VMs and practice making, exploiting then fixing various attack paths that you have learnt about across CRTP / CRTE / PACES. Not only is this a great learning tool, it will help you with the defense portion of the exam (the exam is weighted 50% attack and 50% defense so you can’t ignore it).
I really liked the exam. As with the lab, it makes you think in new ways and the defense side of it is very interesting and was a great learning experience.
Summary
With this blog post I wanted to help you decide which is for you and I hope you are as excited about the labs as I was when I read about them.
If you are completely new to hacking, then I recommend playing with vulnhub / HacktheBox (or even PentesterAcademy’s CTF.live) and learning more about hacking in general and the workflow. Whilst you could do CRTP with no experience, having a decent grounding in hacking techniques in general will help you get the most out of it.
If you are familiar with hacking in general (only basics needed) but have little or no experience with attacking Active Directory (AD) then definitely take CRTP and you will get a lot from it.
If you are very comfortable with the standard attack paths in Active Directory and have maybe done a HtB Pro-lab or two, then take the CRTE and you will find that more valuable without the walkthrough and with the additional flags.
If you look at the syllabus of CRTP and CRTE and you feel like they are beneath you because you are a god of AD, then take PACES. I can promise you it will challenge you in ways that most real world environments won’t and I am sure you will learn a thing or two. Especially if you do this with a C2 as it is actually more difficult with a C2 than without and you need to have a lot of cobalt strike tricks up your sleeve to use it effectively here!
If you are still uncertain on what to take and have the budget then do all three like I did. That way you will be sure you have all the material and all the labs to play around in and that you aren’t missing out.
If you don’t have the budget and need to pick one then I hope this blog post helps out with knowing which level is for you.
If you have any questions then feel free to find me on LinkedIn (link to the side of the post) and ask me there. I won’t give away spoilers or help though!